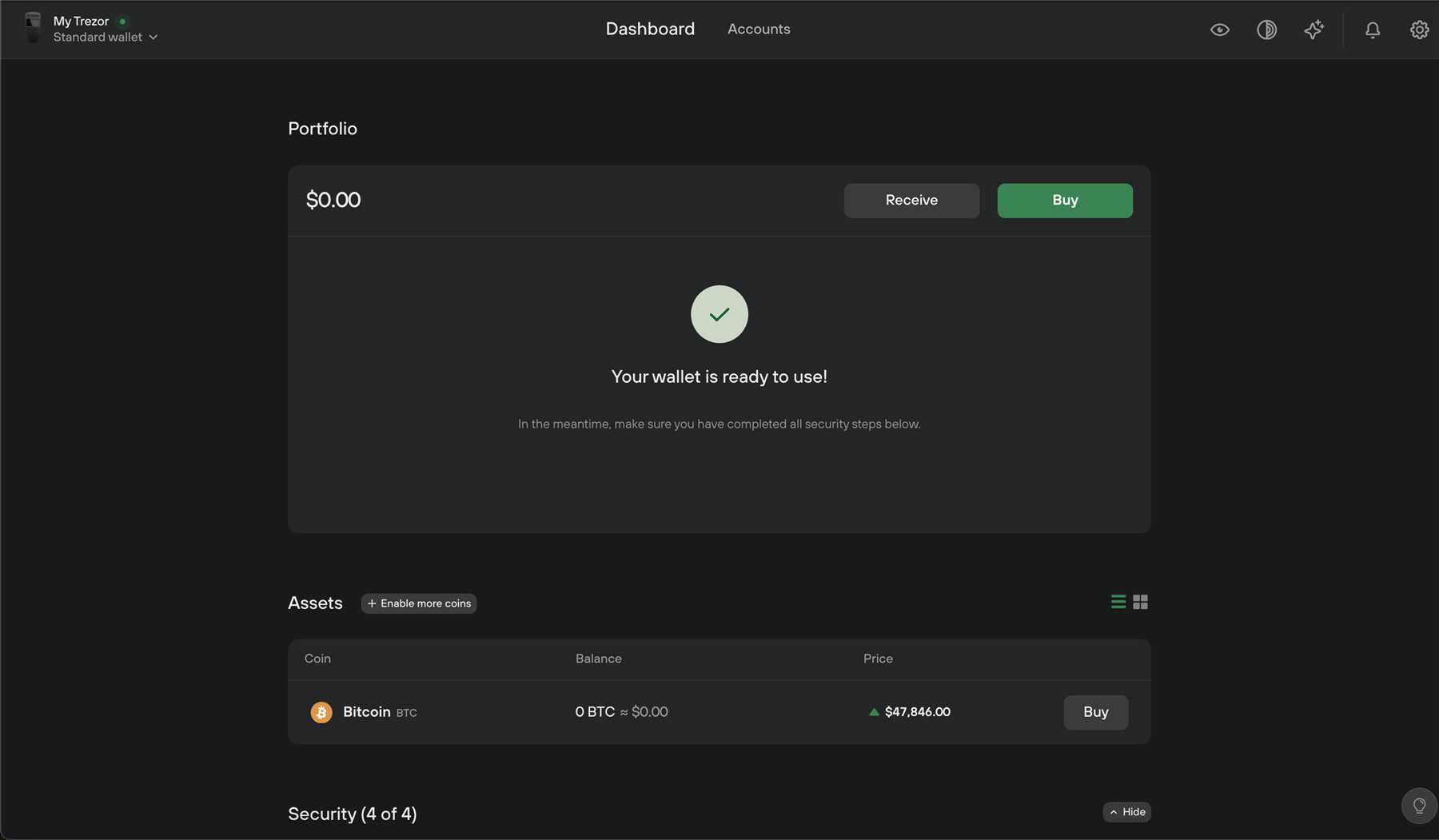
Trezor is a popular hardware wallet used for securing cryptocurrencies. But how exactly does it work? In this article, we will delve into the details of how Trezor functions and how it provides a secure environment for storing your digital assets.
At its core, Trezor is a small device that stores your private keys offline, away from potential hackers and malware. When you want to make a transaction, you connect your Trezor to a computer or mobile device and use it to sign the transaction with your private key, ensuring that your funds remain secure.
But that’s not all – Trezor also has additional security features such as a PIN code and passphrase, further protecting your digital assets from unauthorized access. With Trezor, you can have peace of mind knowing that your cryptocurrencies are safe and sound.
What is Trezor

Trezor is a hardware cryptocurrency wallet that offers secure storage for your digital assets, such as Bitcoin, Ethereum, and other cryptocurrencies. It is a small physical device that connects to your computer or smartphone to securely store your private keys offline, away from potential hackers and malware.
Trezor is known for its ease of use and high level of security, making it a popular choice among cryptocurrency enthusiasts. It provides an extra layer of protection against unauthorized access and provides peace of mind knowing that your funds are safe and secure.
Benefits of Using Trezor
When it comes to safeguarding your cryptocurrencies, using a hardware wallet like Trezor offers a range of benefits. Here are some advantages of using Trezor:
| 1. | Enhanced security: Trezor provides a secure offline storage solution, keeping your private keys away from potential online threats. |
| 2. | User-friendly interface: Trezor’s intuitive interface makes it easy for both beginners and experienced users to manage their digital assets. |
| 3. | Multi-currency support: Trezor supports a wide range of cryptocurrencies, allowing you to store different coins in one device. |
| 4. | Backup and recovery options: Trezor offers seamless backup and recovery processes to ensure that your funds are always retrievable. |
| 5. | Trusted reputation: Trezor is a well-known and reputable hardware wallet brand in the crypto industry, giving users peace of mind. |
Overall, using Trezor can provide you with peace of mind knowing that your digital assets are secure and easily accessible when needed.
How to Set Up Trezor
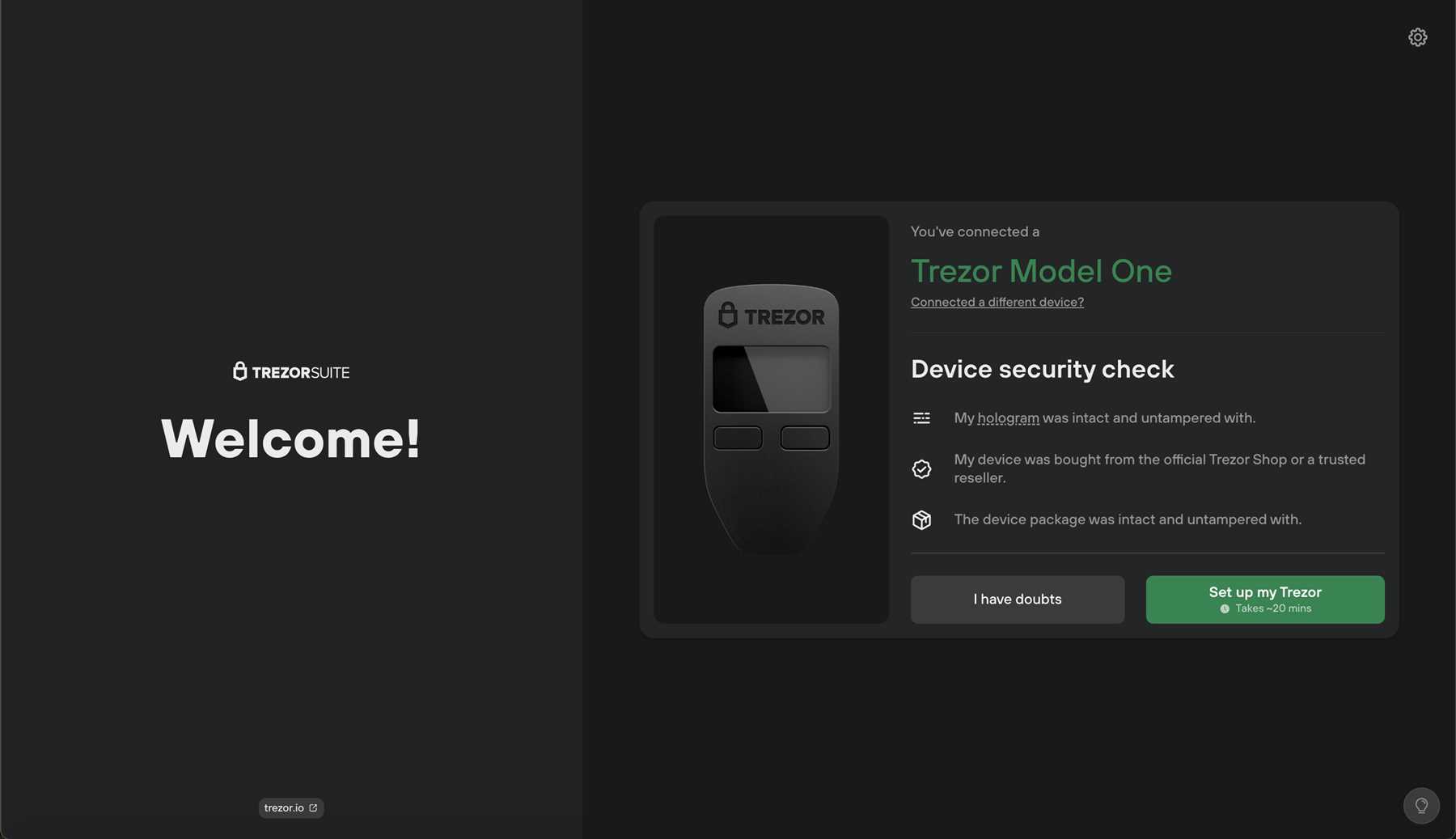
If you’ve just purchased a Trezor hardware wallet and are ready to set it up, follow these simple steps:
- Unbox your Trezor device and connect it to your computer using the USB cable provided.
- Visit the Trezor website and download the Trezor Bridge software for your operating system.
- Install the Trezor Bridge software on your computer and follow the on-screen instructions.
- Once the software is installed, open the Trezor Wallet webpage and create a new wallet.
- Follow the instructions on the webpage to set up your wallet, including creating a secure PIN and writing down your recovery seed.
- Once your wallet is set up, you can start sending and receiving cryptocurrency securely using your Trezor device.
Remember to keep your recovery seed safe and never share it with anyone to protect your funds.
Security Features of Trezor
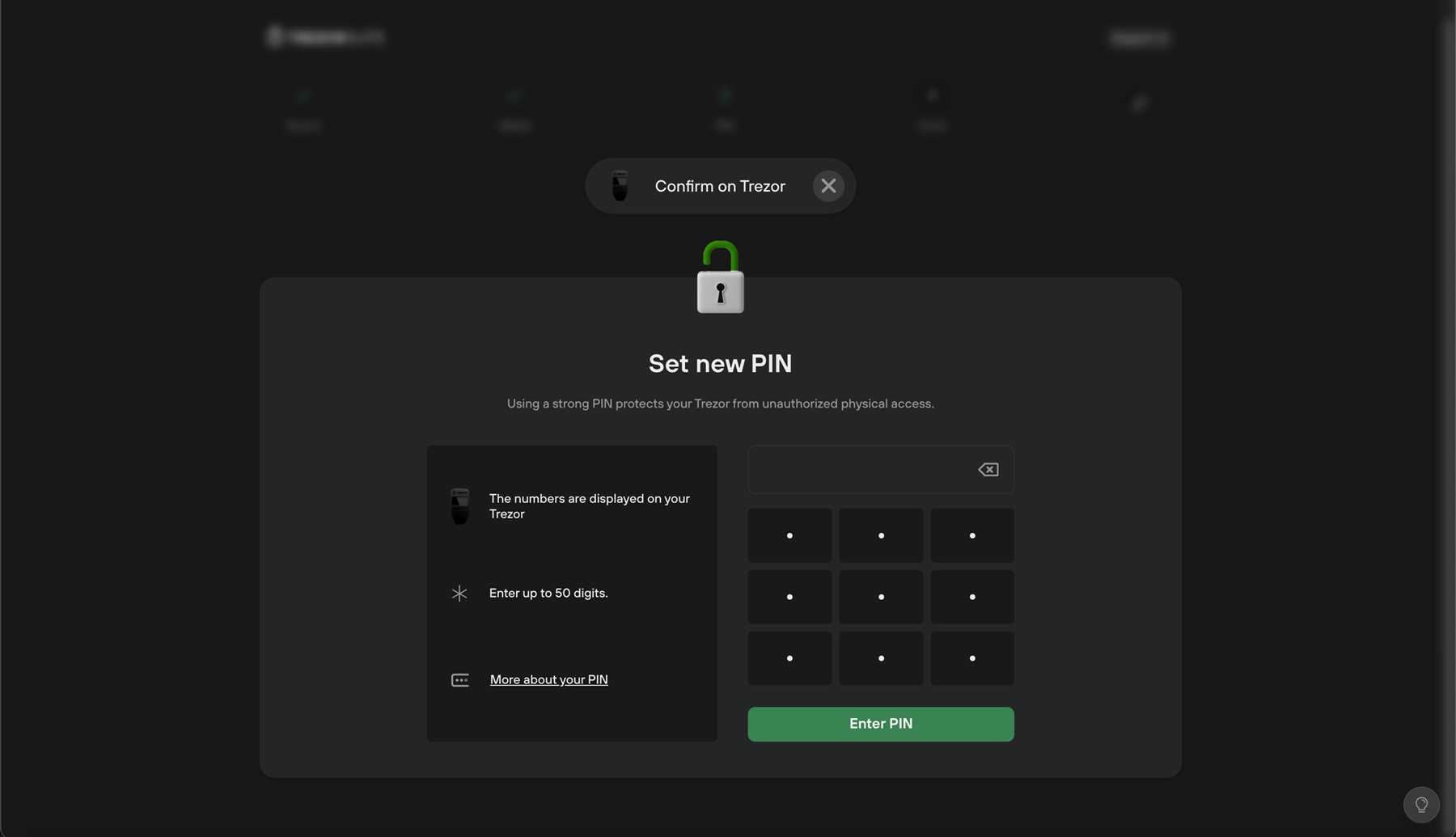
Trezor is renowned for its state-of-the-art security features that ensure the safety of your digital assets. Here are some of the key security features of Trezor:
Secure Element: Trezor devices are equipped with a secure element that protects the private keys and ensures that they never leave the device.
Pin Protection: Users can set up a PIN to prevent unauthorized access to their device and funds.
Passphrase Protection: An additional layer of security can be added with a passphrase, which encrypts the private keys and adds an extra security measure.
Backup and Recovery: Trezor devices come with a recovery seed that can be used to recover the wallet in case the device is lost or damaged.
Open Source Software: The firmware of Trezor devices is open source, allowing for transparency and independent verification of the code.
With these robust security features, Trezor provides a secure and reliable solution for managing your cryptocurrencies.
How to Use Trezor Safely

When it comes to using your Trezor hardware wallet safely, there are a few key steps you should take to ensure the security of your cryptocurrency assets.
1. Set up your Trezor correctly: Make sure to follow the instructions carefully when setting up your Trezor device. This includes creating a strong and unique PIN, writing down your recovery seed in a secure location, and enabling additional security features like passphrase encryption.
2. Keep your firmware up to date: Regularly update the firmware of your Trezor device to ensure that it is protected against any known vulnerabilities. Trezor regularly releases firmware updates to improve security and functionality.
3. Verify transactions on your Trezor: Always verify and double-check any transactions on your Trezor device before confirming them. This helps prevent unauthorized transactions and ensures that you are sending funds to the correct address.
4. Avoid sharing your recovery seed: Your recovery seed is the key to accessing your cryptocurrency funds in case your Trezor is lost or damaged. Never share your recovery seed with anyone and store it in a secure and private location.
5. Use strong passwords and enable two-factor authentication: Strengthen the security of your cryptocurrency accounts by using strong passwords and enabling two-factor authentication wherever possible. This adds an extra layer of protection to your funds.
By following these safety tips, you can use your Trezor hardware wallet with confidence and keep your cryptocurrency assets secure.
Trezor vs. Other Hardware Wallets
When it comes to hardware wallets, Trezor stands out as one of the most popular and trusted options on the market. Its reputation for security, usability, and reliability has made it a top choice for many cryptocurrency users.
One key advantage of Trezor compared to other hardware wallets is its open-source nature. This means that the code used in Trezor devices is publicly available for scrutiny by developers and security experts, enhancing transparency and trust in the device’s security features.
Additionally, Trezor supports a wide range of cryptocurrencies, making it a versatile option for users with diverse cryptocurrency portfolios. Its user-friendly interface and simple setup process also make it accessible to both beginners and advanced users.
While Trezor offers many benefits, it’s important to consider other hardware wallets on the market as well. Ledger, another popular hardware wallet brand, also provides strong security features and supports a wide range of cryptocurrencies. Users may prefer Ledger for its compact design, interface, or specific features that align with their needs.
Ultimately, the choice between Trezor and other hardware wallets comes down to individual preferences, priorities, and security considerations. Both Trezor and other hardware wallets have their strengths and weaknesses, so it’s essential for users to research and determine which option best fits their requirements.
FAQ:
What is a Trezor?
Trezor is a hardware cryptocurrency wallet that provides secure storage for your digital assets. It allows you to store your private keys offline and protect them from hacking attempts.
How does Trezor work?
Trezor works by generating and storing private keys offline in a secure environment. When you want to make a transaction, you connect your Trezor device to a computer or smartphone and sign the transaction with your private key, which is never exposed to the internet.